The digital world is changing fast and with organizations facing an average of 1,636 cyber-attacks per week—a 30% year-over-year increase—cybersecurity is now a top priority. As more enterprises transition to cloud environments, they must equip themselves with the right defenses and skills to effectively combat these risks. This blog is a rundown of strategies and technologies that can help businesses guard their digital assets, ensure compliance, and respond effectively to incidents. We’ll also peek into what’s next for cloud security.
Understanding Cyber Threats and Extracting Actionable Insights
The year 2023 counted 6.06 billion malware attacks, and that’s just one kind of cyber threat. To protect your business today, you first need to comprehend the nature of these threats and how they evolve. Cyber threats come in many forms, from ransomware and phishing attacks to more sophisticated intrusions like advanced persistent threats (APTs).
The secret to fighting off these threats is extracting valuable, actionable insights from your security data.
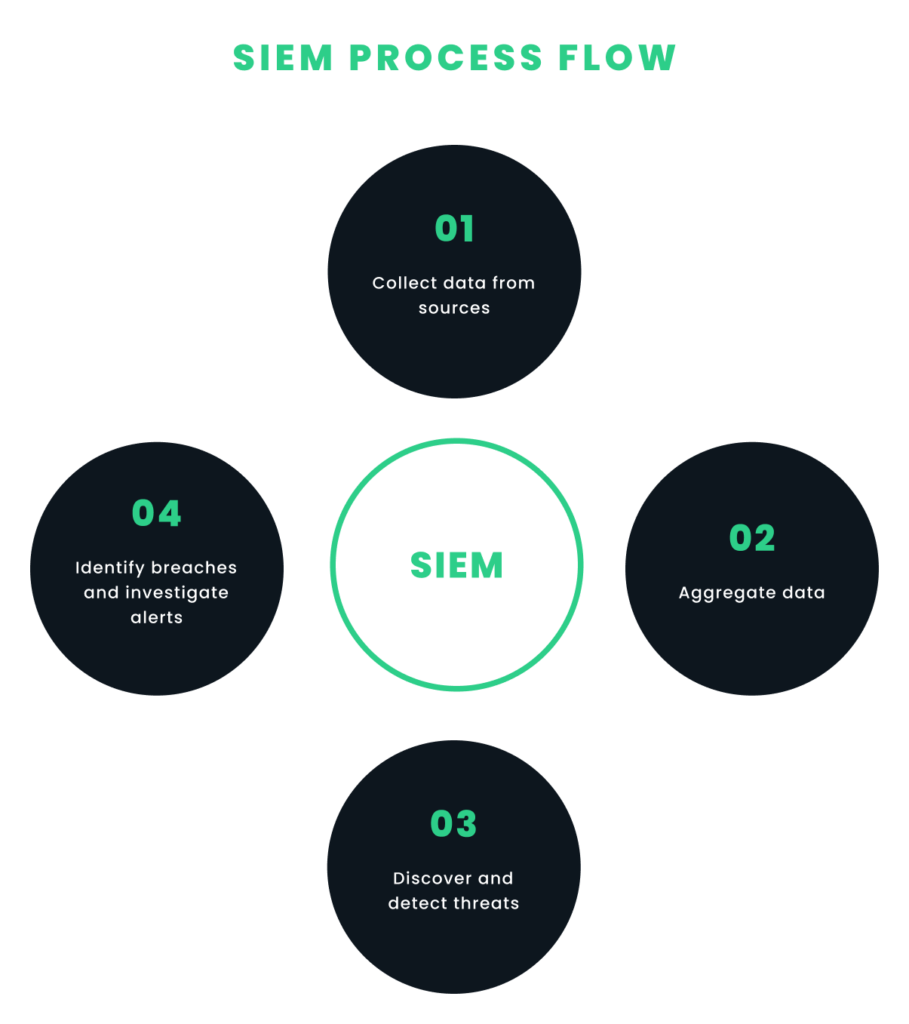
Security Information & Event Management, or SIEM systems, coupled with advanced analytics, can help organizations detect and analyze suspicious activities in real-time. These tools allow businesses to see patterns, forecast possible threats, and take action to stop breaches before they occur. It’s crucial to share these insights with stakeholders, showing how security threats affect the business and why a strong cybersecurity plan matters.
Protecting Your Business with Cloud Security
Cloud security has shifted from a trend to a must-have for today’s businesses. Given the increased adoption of cloud computing, keeping cloud environments safe becomes a top concern. Cloud security covers a wide range of practices, which include data encryption, identity and access management (IAM), and continuous monitoring.
Data Encryption is the first line of defense, making sure that even if data is intercepted, it remains unreadable to unauthorized users. IAM makes certain that approved staff can get into sensitive data and apps, which lowers the chance of insider risks. Continuous monitoring allows for real-time detection of vulnerabilities and threats, enabling swift incident response.
5 Ways to Strengthen Your Cloud Security
“98% of web applications can be attacked, spreading malware and leading users to dangerous websites, showing just how common cyber risks are.”
To boost your cloud security, you need to take a multi-layered approach that combines advanced technologies with smart practices. Here’s a look at some effective strategies and tools that can make a big difference:
1. Advanced Threat Detection and Response:
- Behavioral Analytics: Detect anomalies by establishing baselines and identifying deviations using machine learning.
- Threat Intelligence: Integrate real-time threat data to anticipate and counter new threats.
- Automated Response: Use SOAR platforms to automate incident response and reduce reaction times.
2. Enhanced Identity and Access Management (IAM):
- Zero Trust Network Access (ZTNA): Verify every access request based on identity, device, and context.
- Adaptive Authentication: Customize authentication requirements based on risk factors such as user location, device, and behavior.
- Privileged Access Management (PAM): Manage and audit privileged accounts to prevent misuse.
3. Advanced Encryption Techniques:
- End-to-End Encryption: Protect data throughout its lifecycle.
- Homomorphic Encryption: Process data while keeping it encrypted.
- Tokenization: Replace sensitive data with secure tokens to reduce exposure.
4. Comprehensive Cloud Security Frameworks:
- Cloud Security Posture Management (CSPM): Assess and manage security configurations and compliance.
- Cloud Workload Protection Platforms (CWPP): Protect virtual machines, containers, and serverless functions.
- Cloud Access Security Brokers (CASBs): Control and monitor cloud application usage with data loss prevention and threat protection.
5. Data Governance and Compliance:
- Dynamic Data Classification: Automatically categorize and protect sensitive information.
- Automated Compliance Auditing: Use tools to continuously monitor and report on compliance.
- Data Sovereignty Controls: Ensure data remains within required geographic boundaries to meet regional regulations.
At Celestial Systems, our Cloud Security solutions are designed to protect your business at every level. From safeguarding data to monitoring cloud environments, we provide robust security solutions tailored to your specific needs of modern enterprises.
Leveraging Microsoft’s Cloud Security Tools
When it comes to cloud security, using tools from established providers like Microsoft can significantly enhance your protection strategy. Microsoft offers a suite of security tools integrated into its cloud services, including Azure Security Center, Microsoft Defender for Cloud, and Microsoft Sentinel.

Azure Security Center delivers comprehensive security management and advanced threat protection for workloads across hybrid cloud environments. Microsoft Defender for Cloud strengthens your multi-cloud and hybrid environments with advanced threat protection and actionable security insights. Azure Sentinel is a scalable, cloud-native SIEM that uses AI to analyze data large volumes, identify anomalies, and respond to incidents in real-time.

By incorporating these tools into your security framework, your business data remains protected, compliant, and resilient against cyber threats.
Future Trends in Cloud Security: What to Expect in 2025 and Beyond
Looking ahead, the world of cloud security is evolving rapidly, with some exciting trends on the horizon:
- AI and Machine Learning Integration: AI and ML will automate threat detection and response, offering enhanced capabilities to analyze massive datasets and identify subtle patterns that may be missed by human analysts. These technologies will enable more proactive threat management by suggesting or even implementing corrective actions in real time. The integration will lead to more adaptive security systems that continuously improve as they learn from new threats.
- Zero Trust Architecture: The Zero Trust model, which assumes that threats could be present both inside and outside the network, is anticipated to become the norm. This approach requires rigorous verification for every access request, regardless of its origin. By treating all network traffic as potentially harmful and continuously validating user and device authenticity, it will cut down the risk of unauthorized access and data breaches.
- Quantum-Resistant Encryption: As quantum computing advances, traditional encryption methods may become vulnerable to decryption by quantum algorithms. Quantum-resistant encryption algorithms are expected to emerge as critical defenses against this new computational power. These algorithms will be designed to withstand the decryption capabilities of quantum computers, ensuring that sensitive data remains protected well into the future.
- Enhanced Data Privacy Regulations: With governments globally enforcing more rigorous data privacy rules, companies must update their cloud security measures to stay compliant. This includes meeting requirements for data protection, breach notifications, and user consent. Failure to do so could result in hefty penalties and loss of customer trust.
- Increased Focus on Supply Chain Security: Cybercriminals are aggressively targeting supply chains to gain access to larger networks. Businesses must strengthen their security measures not only within their own systems but also across their entire supply chain. This involves implementing rigorous security protocols for third-party vendors, monitoring supply chain activities for suspicious behavior, and ensuring that all partners adhere to robust security standards.
At Celestial Systems, we aim to lead the way in these new developments, ensuring that our customers are equipped with the latest tools and strategies to safeguard their digital assets. Our Cloud Solutions include Application Transformation, Infrastructure Modernization, and Cloud AI, all designed with security as a top priority.
The Path Forward
As cyber threats continue evolving, businesses must stay alert and take proactive actions to keep their cloud safe. By understanding the nature of these threats, leveraging advanced security tools, and staying informed about future trends, you can protect your business and ensure its continued success. Regularly assessing and reviewing security measures, implementing multi-layered defenses, and adopting a culture of cybersecurity awareness will serve businesses in the long run.
For more information on how Celestial Systems can help you secure your cloud environments, please visit our Contact Us page or explore our comprehensive Cloud Security solutions.

