Web applications hold a critical role today, as they navigate and mold the trajectory of our digital interactions. But with great opportunities come great responsibilities, especially when it comes to security. Why does it matter so much?
Imagine websites facing constant cyber threats, leading to downtime, data breaches, and financial repercussions. In this digital age, robust web application security becomes the key to preserving user trust, organizational credibility and ensuring the uninterrupted functionality of applications.
Why is SecOps Crucial in Modern Web App Development?
Before delving into challenges, it’s crucial to recognize the importance of SecOps in the development process.
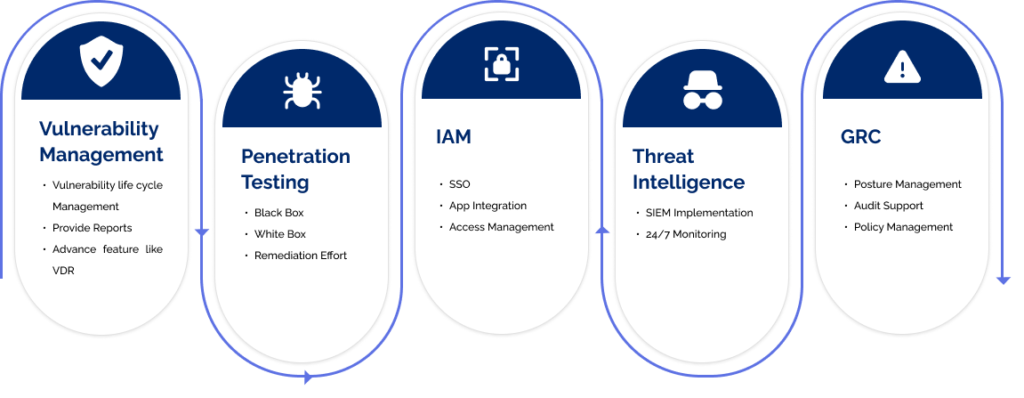
- Vulnerability Management: By consistently monitoring and mitigating vulnerabilities, SecOps ensures a robust defense against potential exploits and unauthorized access, enhancing the overall security posture.
- Penetration Testing: Essential to simulate real-world cyber threats, it provides insights that strengthen security defenses, validate resilience, and proactively fortify web applications against potential attacks.
- IAM (Identity and Access Management): IAM enhances data security by ensuring only authorized individuals have appropriate access privileges, preventing unauthorized breaches in modern web app development.
- Threat Intelligence: Threat Intelligence provides real-time insights that enable proactive defense strategies, protecting web applications from emerging risks and vulnerabilities.
- GRC (Governance, Risk, and Compliance): As a foundational element of SecOps, GRC ensures that security practices align with industry regulations and organizational policies, prevents legal repercussions, and protects the reputation of organizations.
- Team Collaboration- Facilitating collaboration between development, operations, and security teams, SecOps ensures shared responsibility and accelerates development cycles.
- Proactive Bug Detection- By integrating security measures from the start, SecOps helps catch potential issues early in the development process, preventing them from becoming bigger problems later.
- Rapid Incident Response- In the event of a security incident, SecOps streamlines the response process, swiftly identifying, containing, and recovering to minimize the impact.
- Agile Integration- Seamlessly aligning with agile and DevOps practices, SecOps enhances the speed and efficiency of development cycles while prioritizing security.
Key Challenges in SecOps Implementation
Implementing Security Operations (SecOps) practices in the context of modern web application development introduces a set of challenges that organizations need to navigate adeptly.
1. Rapid Development Cycles
In the era of Agile and DevOps, the pace of web application development is unprecedented. Rapid releases and continuous deployment pose a significant challenge for security teams to keep up with the speed without compromising security measures.
2. Integration with DevOps Practices
Harmonizing SecOps seamlessly with DevOps practices is a crucial challenge. Bridging the gap between traditionally distinct security and development teams and incorporating security as a collaborative element in the continuous integration/continuous deployment (CI/CD) pipeline, demands organizational and cultural adjustments.3. Complex Application Architectures
Modern web applications are complex, often built on microservices architectures and utilizing various third-party APIs. Securing these intricate systems poses challenges in terms of visibility, monitoring, and ensuring consistent security across all components.
4. Automation and Orchestration
While automation is integral to DevOps success, integrating automated security processes into development pipelines can be challenging. Orchestrating security measures without hindering development speed requires careful planning and implementation.
5. Threat Intelligence and Adaptability
The ever-evolving threat landscape demands constant vigilance. SecOps teams face the challenge of staying abreast of the latest threat intelligence, adapting security measures accordingly, and ensuring that web applications remain resilient to emerging threats.
6. Securing Third-Party Components
Modern web applications often rely on third-party components and libraries. Ensuring the security of these components, which may have their update cycles and vulnerabilities, poses a significant challenge for SecOps teams.
Overcoming SecOps Challenges
1.Shift-Left Security:
Integrating security measures earlier in the development process, known as “shift-left,” is an effective strategy. This involves incorporating security into the planning and design phases, reducing vulnerabilities before they reach the production stage.
2.Continuous Monitoring and Testing:
Implementing continuous monitoring and testing practices helps identify vulnerabilities and security issues early in the development lifecycle. Automated testing tools can be utilized to perform security scans and checks at various stages of development.
3.Security as Code:
Implementing security as code involves treating security policies and measures as code artifacts. This enables security controls to be versioned, tested, and integrated into the development pipeline, ensuring consistency and repeatability.
4.Incident Response Planning:
Having a well-defined incident response plan is essential. This includes procedures for identifying, responding to, and mitigating security incidents promptly.
5.Education and Training:
Addressing the human factor is crucial. Providing ongoing education and training for development and operations teams on security best practices ensures that everyone is equipped to contribute to a secure development environment.
The Road Ahead: Enhancing SecOps in Modern Web App Development
In conclusion, while the challenges in implementing SecOps in modern web app development are substantial, adopting a proactive, collaborative, and strategic approach allows organizations to build robust security. From cultural shifts to embracing automation and continuous monitoring, organizations must prioritize security throughout the development lifecycle. By doing so, they not only safeguard their applications but also contribute to a more secure digital ecosystem.
1. Read our sample case study – Leading Tech product company prepares for a SAAS offering by updating and automating SecOps.
2. Contact us for a “Data, InfoSec and Compliance Assessment”. This is a unique offering that covers –
Scope: Data Discovery & Analysis, Review of Applications
Insights Delivered: Scan findings across On-premises and Cloud Services, Data Security and Compliance Recommendations and Approach Plan in accordance with the Center for Internet Security (CIS) Framework, including the NIST Cybersecurity Framework (CSF) and NIST SP 800-53, the ISO 27000 series of standards, PCI DSS, HIPAA, and others.


